Member-only story
Snake&Apple IV — Dylibs
Automating Dylib Hijacking detection with Python.
INTRO
Welcome to another article in the series on macOS security internals!
In the Snake&Apple I — Mach-O, I briefly introduced Load Commands, which provides Dynamic Loader (dyld) information on Dynamic Libraries (dylibs) without further explanation. This article will go deep into the concept of libraries and explain the Dylib Hijacking vulnerability.

Toward the end, I will share my implementation of a Dylibtree tool and automatic Dylib Hijacking scanner, which example output is below:
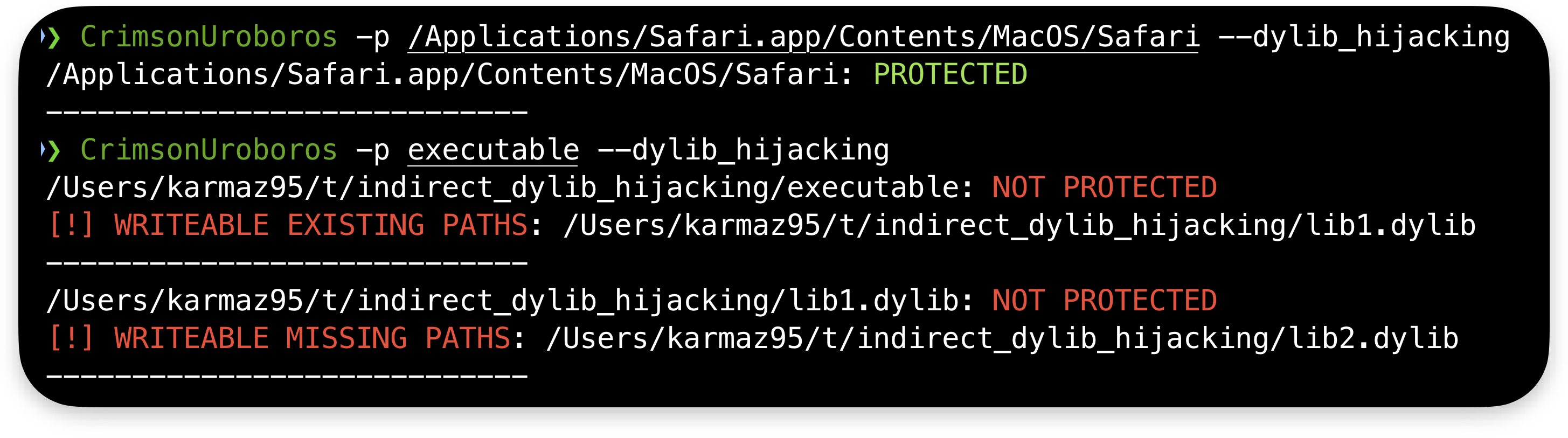
Please note that some topics have been intentionally omitted and will be addressed in future articles. However, leave a comment if you have any questions or need clarification about anything written here while reading. I guarantee a response and will use your feedback for future articles.
The Snake&Apple IV. Dylibs repository contains all of the code used.
Libraries — Static vs Dynamic
In programming, a library is a collection of precompiled code. It provides a reusable set of functionalities for executables and other libraries.

Static Library
It contains object code directly linked with the program at compile time. During the linking phase, the contents of a static library are copied into the executable file, making the resulting file larger but self-sufficient, as it doesn’t require any external dependencies at runtime.

Any changes made to a static library require recompiling the entire program.